NVIS AI creates secure,
invisible networks in minutes
Deploy Zero Trust easily & with better security than VPNs
Securing businesses & service providers worldwide

Simple & fast
Easily deploy Zero Trust Network Access (ZTNA)
Installs in minutes
AI removes the need for
skilled techs to configure
Work out of the box
No need to change
your network or workflows

Fast performance
All resources are connected
direct peer-to-peer

No public attack surface
Hackers can't hack what they can't see.
Be NVISible from current & future threats.
Hide your public IP
Avoid being blocked,
sniffed, or traced
Be NVISible
Layer 2 encryption hides the source, destination, & traffic

No logs
Avoid exploit as we don't
collect or store your info

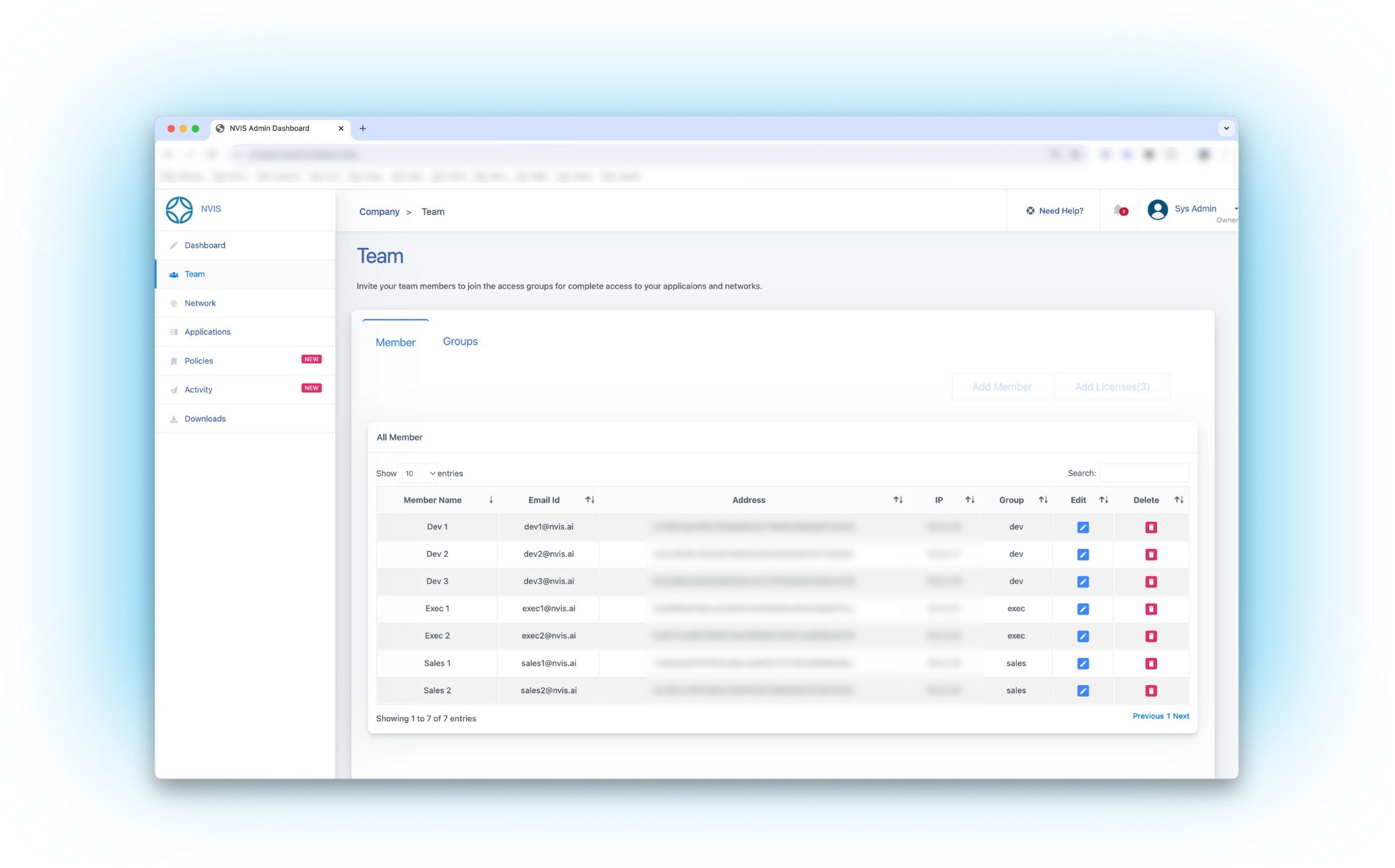
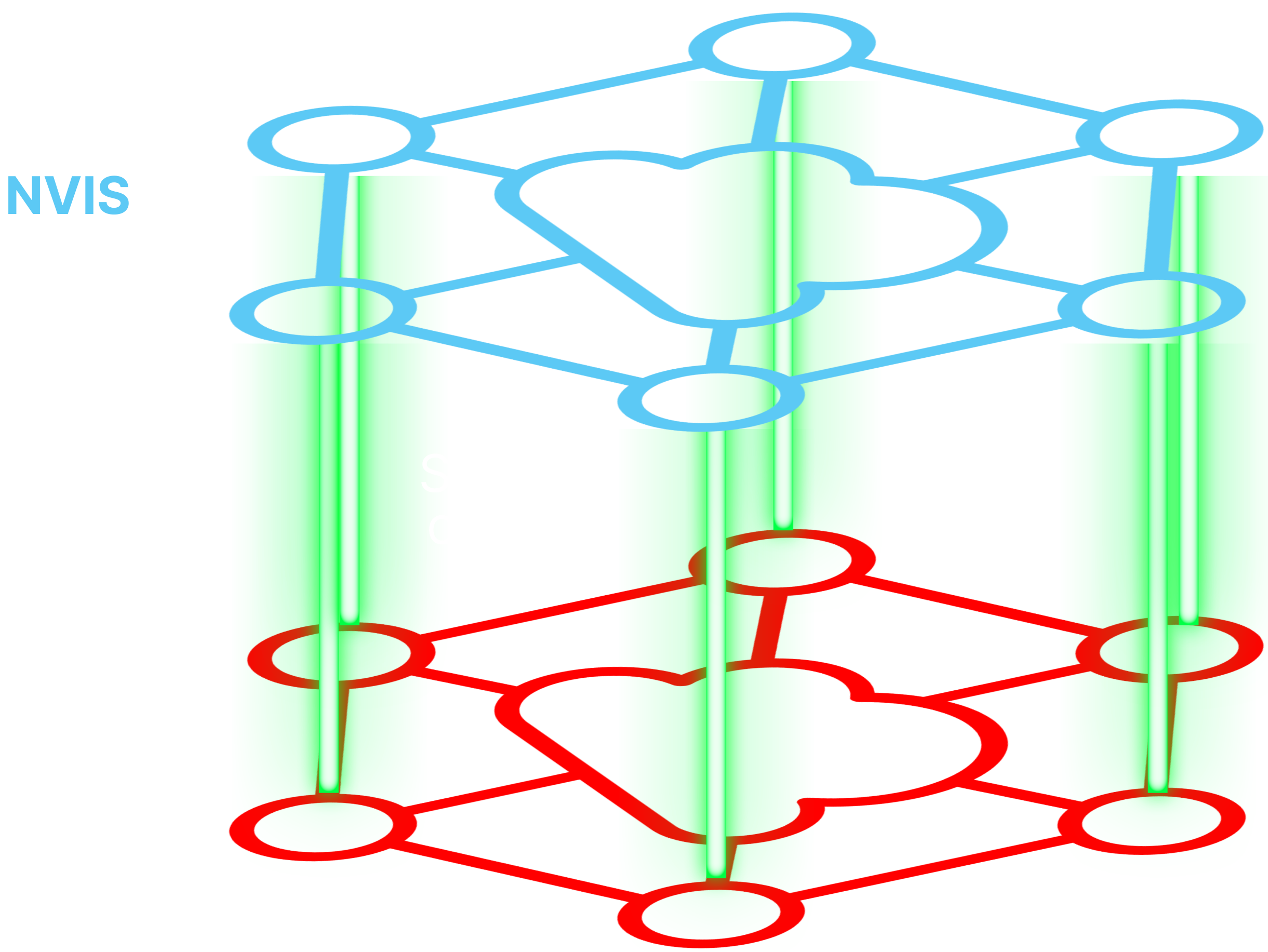
Universal access
Any resource. Anywhere.
Connect any resource
Universally connect on-prem, cloud, OT, & edge resources
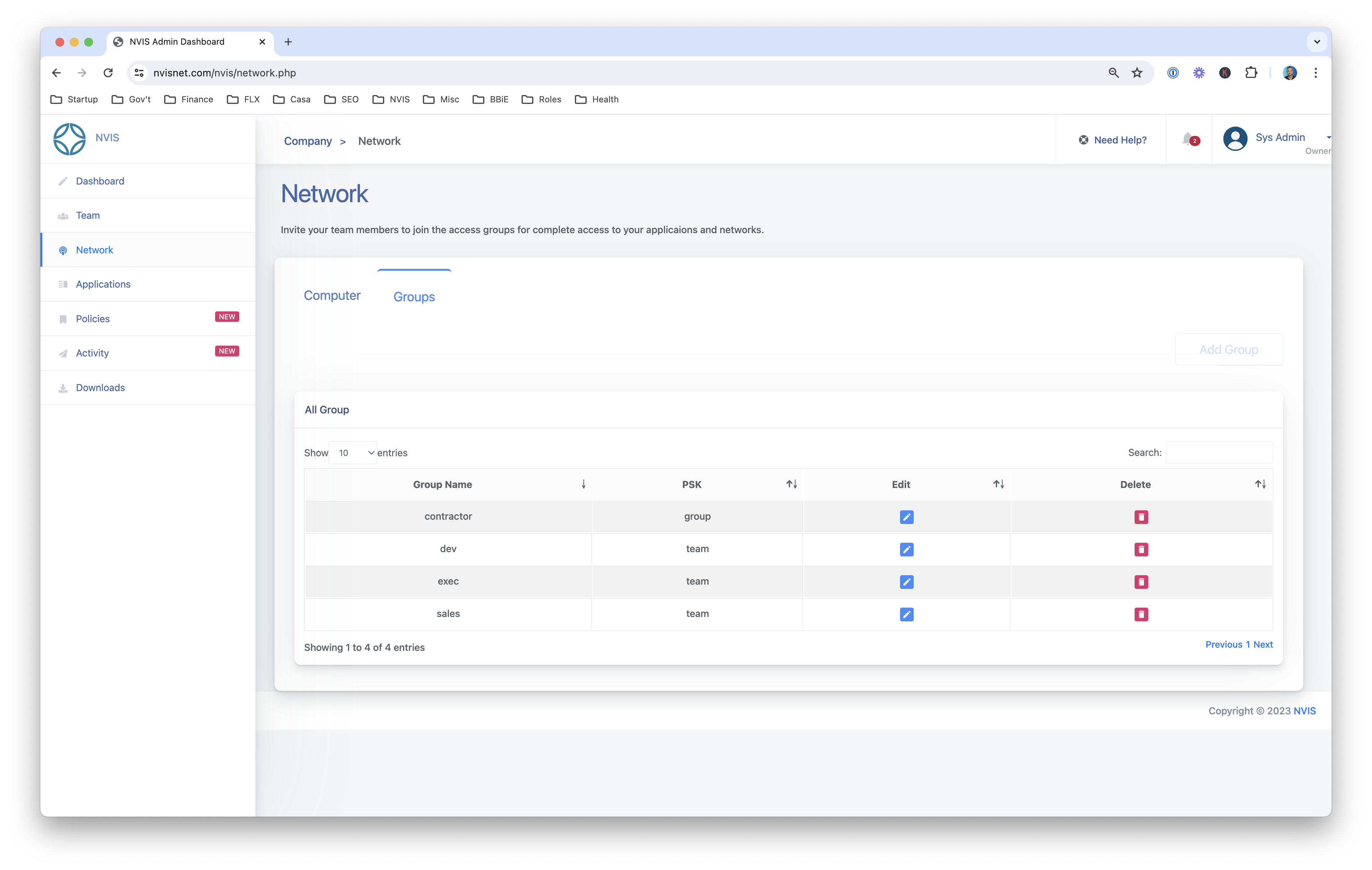
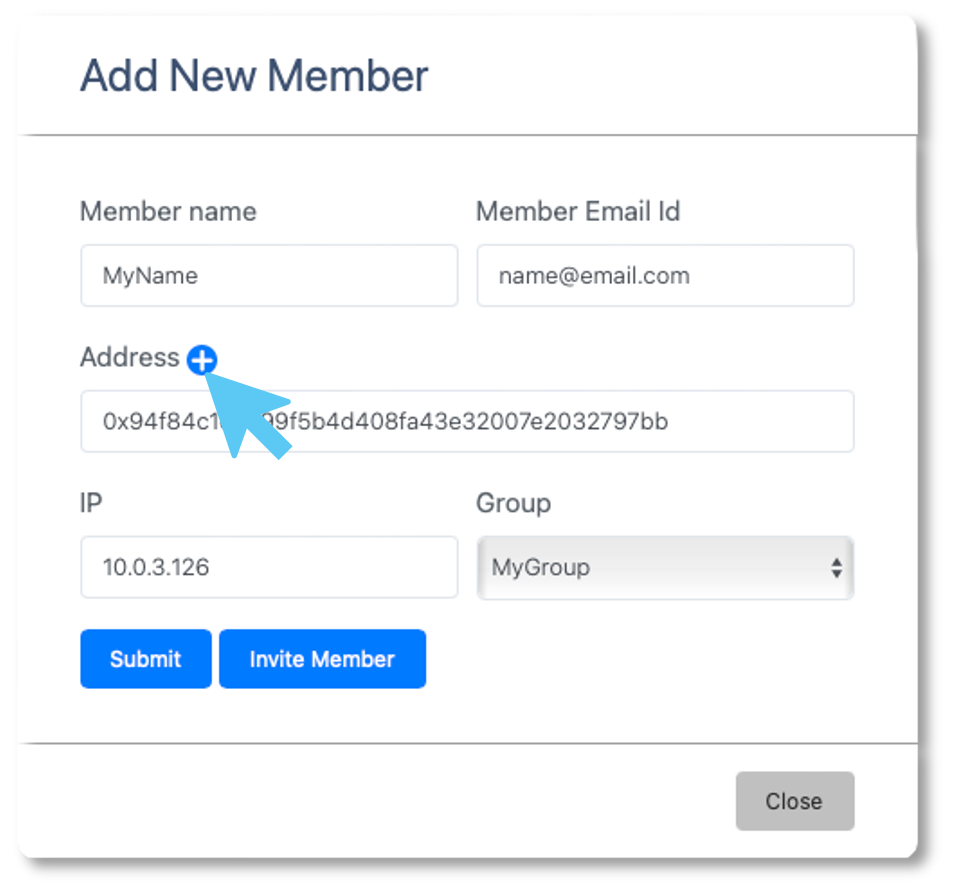
Control access
Easily onboard/off-board contractors & third parties

Be anywhere
Connect to any resource
globally without blocks
Say bye to VPNs
All the pros. Without the cons.
VPN
Vulnerable to attacks
No access control
Slow (routing)
Complex
High TCO
Censorable

No public attack surface
Zero Trust
Fast (P2P)
Simple
Low TCO
Uncensorable
Frequently Asked Questions
Q: Has NVIS AI been independently tested and certified?
Yes, NVIS AI has been independently tested and certified by Miercom Labs, a respected test lab specializing in network security and performance. Our service has been field-tested globally, including in regions such as China, Russia, and Saudi Arabia, ensuring reliable and secure access for hundreds of users worldwide.

Does NVIS AI log or store customer data?
NVIS AI does not handle or store customer data. Any necessary logging is conducted solely on user endpoints, and NVIS operates as a secure overlay network without touching or accessing customer information.

How does NVIS AI align with terms of service (TOS) and privacy regulations?
NVIS AI prioritizes ethical security practices and adheres to the terms of service for all platforms. We operate similarly to the Internet Assigned Numbers Authority (IANA) for private networks, ensuring we enforce compliance, transparency, and integrity across all interactions.

What is NVIS AI’s approach to user privacy and data handling?
NVIS AI offers robust security, not secrecy. Our service is designed for secure, private access while respecting user and platform terms. We maintain transparent operations, protecting users without compromising regulatory compliance.

Does NVIS AI monitor or track user traffic?
No, communication with NVIS AI is exclusively peer-to-peer, ensuring that we have no access to, and do not track, user traffic. NVIS AI’s architecture is built to ensure privacy and security without intrusion into user activities.

Can NVIS AI impact regular internet service or troubleshooting?
No, because NVIS AI functions as an overlay network, it does not interfere with underlying internet service. Endpoint owners can continue to test and debug their internet services independently, with NVIS AI running securely alongside.


The next-gen VPN your team will enjoy.
Be NVISible.


NVIS AI creates secure, invisible networks in minutes
Deploy Zero Trust easily &
with better security than VPNs

Securing businesses & providers worldwide


Simple & fast
Easily deploy Zero Trust
Network Access (ZTNA)

Installs in minutes
AI makes it easy for even
non-ITs to configure

Works out of the box
No need to change your
network or workflows

Fast performance
All resources are connected
direct peer-to-peer

No Public
Attack Surface
Hackers can't hack what they can't see.
Be NVISible from current & future threats.

Hide your public IP
Avoid being blocked,
sniffed, or traced

Be NVISible
Layer 2 encryption hides the
source, destination, & traffic

No logs
Avoid exploit as we don't
collect or store your info

Universal access
Any resource. Anywhere.

Connect any resource
Universally connect on-prem,
cloud, OT, & edge resources

Control access
Easily onboard/off-board
contractors & third parties

Be anywhere
Connect to any resource
globally without blocks

Say bye to VPNs
All the pros.
Without the cons.
VPN
Vulnerable to attacks
No access control
Slow (routing)
Complex
High TCO
Censorable

No public attack surface
Zero Trust
Fast (p2p)
Simple
Low TCO
Uncensorable

Frequently Asked Questions
Q: Has NVIS AI been independently tested and certified?
Yes, NVIS AI has been independently tested and certified by Miercom Labs, a respected test lab specializing in network security and performance. Our service has been field-tested globally, including in regions such as China, Russia, and Saudi Arabia, ensuring reliable and secure access for hundreds of users worldwide.

Does NVIS AI log or store customer data?
NVIS AI does not handle or store customer data. Any necessary logging is conducted solely on user endpoints, and NVIS operates as a secure overlay network without touching or accessing customer information.

How does NVIS AI align with terms of service (TOS) and privacy regulations?
NVIS AI prioritizes ethical security practices and adheres to the terms of service for all platforms. We operate similarly to the Internet Assigned Numbers Authority (IANA) for private networks, ensuring we enforce compliance, transparency, and integrity across all interactions.

What is NVIS AI’s approach to user privacy and data handling?
NVIS AI offers robust security, not secrecy. Our service is designed for secure, private access while respecting user and platform terms. We maintain transparent operations, protecting users without compromising regulatory compliance.

Does NVIS AI monitor or track user traffic?
No, communication with NVIS AI is exclusively peer-to-peer, ensuring that we have no access to, and do not track, user traffic. NVIS AI’s architecture is built to ensure privacy and security without intrusion into user activities.

Can NVIS AI impact regular internet service or troubleshooting?
No, because NVIS AI functions as an overlay network, it does not interfere with underlying internet service. Endpoint owners can continue to test and debug their internet services independently, with NVIS AI running securely alongside.